Difference between revisions of "Exe0.1 Eric Snodgrass"
| Line 74: | Line 74: | ||
'''notes''' | '''notes''' | ||
<div id="fn1"></div> [1] A stored-program computer for the processing, transmission and recording of inputs and outputs in which numerically encoded program instructions and data are stored in the same read-write, random-access memory and accessible via a common bus. Thus in real mode, | <div id="fn1"></div> [1] A stored-program computer for the processing, transmission and recording of inputs and outputs in which numerically encoded program instructions and data are stored in the same read-write, random-access memory and accessible via a common bus (though the application of protected mode style features is not limited to von Neumann architectures). For specific discussions of protected mode style features, see things such as the various NX bit ("No-eXecute") technologies used in CPUs to segregate areas of memory for use by either storage of processor instructions or for storage of data. Via such forms of segregation, such a memory protection feature can then mark certain areas of memory as non-executable. Thus in "real mode," a user should ostensibly be able to access and address all areas of the memory without any protection mechanism being employed. Like the tightly wound psychoanalytical schematics of Jacques Lacan, protected mode can be seen to act here "as both the enemy and co-existent partner of a Real Mode" (Kittler 2006, p.359-60). As Howse's work makes clear, the very notion of a protected mode might be questioned at several levels. | ||
<div id="fn2"></div> [2] Accompanying statement to [https://vimeo.com/86690846 a short video by Howse] on the ptrace() call: "Date of origin: 1979. Author/inventor/context: Seventh Edition Unix, Bell Laboratories. An operating system call, first implemented in Version 7 of AT&T UNIX in 1979, which allows one piece of software (the parent) to observe, control, examine and alter any aspect of another process running on the same operating system. The ptrace call is commonly used to debug running code and can be considered as an active language, infiltrating and interrogating, snooping on and injecting code into living, running processes; an active language projecting a potential process promiscuity within the machine. Ptrace shifts the site of execution and is nowadays commonly viewed as an unnecessary security risk." | <div id="fn2"></div> [2] Accompanying statement to [https://vimeo.com/86690846 a short video by Howse] on the ptrace() call: "Date of origin: 1979. Author/inventor/context: Seventh Edition Unix, Bell Laboratories. An operating system call, first implemented in Version 7 of AT&T UNIX in 1979, which allows one piece of software (the parent) to observe, control, examine and alter any aspect of another process running on the same operating system. The ptrace call is commonly used to debug running code and can be considered as an active language, infiltrating and interrogating, snooping on and injecting code into living, running processes; an active language projecting a potential process promiscuity within the machine. Ptrace shifts the site of execution and is nowadays commonly viewed as an unnecessary security risk." | ||
Revision as of 08:12, 14 April 2016
//some ongoing notes on execution for *.exe (ver0.1) meetup
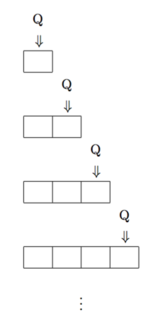
sites of execution: instruction pointer
Execution. The act of carrying out a set of instructions.
Execution. The act of carrying out a set of instructions in a step by step fashion.
Execution. The automated act of cycling through a set of machine-readable instructions in a step by step fashion.
Execution. The automated act of cycling through a set of machine-readable instructions (logically encoded character-chains fetched from stored-program memory) in a step by step fashion (making calls upon the memory for relevant operators and storing any resultant operands back in memory).
Execution. The automated act of cycling sequentially (in a time co-ordinated process) through a set of machine-readable instructions (logically encoded character-chains fetched from stored-program memory) in a step by step fashion (making calls upon the memory for relevant operators and storing any resultant operands back in memory), whereby any actions are made effectively decidable according to the parameters of the active instruction set.
Execution. The automated act of cycling sequentially (in a time co-ordinated process determined via a pulse whose period is established by a phase distributor) through a set of machine-readable instructions (logically encoded character-chains fetched from stored-program memory) in a step by step fashion (making calls upon the memory for relevant operators and storing any resultant operands back in memory), whereby any actions are made effectively decidable (capable of being interpreted by a logical decoder whose signals address the instruction pointer to the component on which the instruction operates) according to the parameters of the active instruction set and repeating such cycles for as long as they continue to remain effectively decidable.
Execution. The automated act of cycling sequentially (in a time co-ordinated process determined via a pulse whose period is established by a phase distributor) through a set of machine-readable instructions (logically encoded character-chains fetched from stored-program memory and placed in the executing command circuits) in a step by step fashion (making calls upon the memory for relevant operators and storing any resultant operands back in memory), whereby any actions are made effectively decidable (capable of being interpreted by a logical decoder whose signals address the instruction pointer to the component on which the instruction operates) according to the parameters of the active instruction set and repeating such cycles for as long as they continue to remain effectively decidable or until there are no more instructions to execute (i.e. the instruction pointer points to the end of the instruction sequence).
sites of execution: pincer
The essence of abstraction is preserving information that is relevant in a given context, and forgetting information that is irrelevant in that context. The key to using abstraction effectively in programming is finding a notion of relevance that is appropriate for both the builder of an abstraction and the potential clients of the abstraction. That is the true art of programming.
– John V. Guttag, Introduction to Computation and Programming Using Python, p.45
shift.
Perched at the verge of some low-hanging brush or on a leaf’s edge: the tick. Dwelling in all of its alien personhood, this “blind and deaf bandit” (Uexküll 2010, p.45) of the outdoors passes days, months, even years in wait of a single blood meal. Charged. Alert. Questing a world of its particular accord.
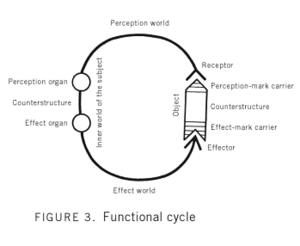
Nevertheless, a few actions on its part direct themselves to certain devotees of pattern recognition. Writing in 1934, Swiss biophilosopher Jakob Johann Baron von Uexküll shares one such notable (and oft-recited) account, taking his reader on an animated foray through what he distinguishes as three sequential “functional cycles” that are initialised somewhere within the tick’s being at the first (perhaps all-enveloping) detection of butyric acid, an odor promiscuously emitted by the skin glands of all mammals and for which the tick, like many other animals, is readily attuned to. Von Uexküll (2010, p.51):
And now something miraculous happens. . . From the enormous world surrounding the tick, three stimuli glow like signal lights in the darkness and serve as directional signs that lead the tick surely to its target. . . Through these features, the progression of the tick’s actions is so strictly prescribed that the tick can only produce very determinate effect marks.
In von Uexküll’s hypothesis, such functional cycles are activated within the environments of the “perception world” and their co-constitutive productive counterparts from the “effect world.” Any nominally organic entity is itself an active subject in the sense that it is able to receive and form "perception marks" from certain objects of its surrounding, which it is able to identify because of some form of functional ability on the entity’s part to potentially act upon these perception marks by turning them into “effect marks."
Thus a tick is known to act on an initial perception mark of butyric acid by launching itself from its perch and, in the case of a successful landing, is able to impress onto the mammal’s hair the effect mark “collision.” This in turn allows for an erasing of the initial perception mark so as to clear the decks for a transition to a new functional cycle in which the tick sets off across the hirsute expanse of its mammalian host, relying on its further sensitivity to temperature to detect the perception mark of a bare patch of pulsing, warm-blooded skin. A sign that, for this bloodborne practitioner of hematophagy, is quite possibly a mark of marks. An event on which to execute the climatic third act of cutting a hole in the host’s epidermis, inserting its harpoon-like hypostome into the skin of its receiver. An interfacing not only of parasite and host, but of mutually executable materials, a layer of skin and the calcified hypostome readily enveloping one another in an embrace that takes no note of any consequences to their host organisms. After all, “The tick’s hearty blood meal is also its last meal” (von Uexküll 2010, p.45).
As von Uexküll (2010, p.48-9) describes it, “Figuratively speaking, every animal subject attacks its objects in a pincer movement-with one perceptive and one effective arm.” Furthermore, the perception and effect worlds are not separate as such, but rather “form one closed unit” - what von Uexküll calls the Umwelt, the subject-specific, materially discursive environment of objects whose executable qualities define the experiences of the executing entity in question. Thus the biophilosophical scientific method being applied here creates a rather robust, pincer-like binding, its abstract functional schema able to unpack (in a readily recursive fashion) the functional cycles and materially discursive Umwelt of any organic entity of its choice.
Such powerful discursive models were in the air at the time. Writing in the very same period as von Uexküll, Alan Turing (1936), in his paper "On Computable Numbers, with an Application to the Entscheidungsproblem," was able to formulate his breakthrough description of computation and a sketch of its practical application in the form of a "univeral machine." As with von Uexküll's functional cycle, there is a pincer-like quality all of its own in Turing's formulation. As Georges Ifrah (2001, p.278-9) neatly explains it, “The real genius of Turing’s invention is the fact that he invented both the abstract form of a revolutionary device and the mathematical concept which allowed the device to be analysed: the theory and its application were unified from the outset. It’s as if Archimedes had invented the principle of the lever and the lever itself at the same moment.” Where von Uexküll (2010, p.42) would regularly (and with much delight) mock behaviourist "machine theorists" and their habit of turning animals "into pure objects", Turing highlights a decisive and powerful vitality of this machine operator by showing its inherent potential to be both an object and subject of its particular devices.
Each to their own Umwelt. And yet, there is a shared beating pulse to each of these formulations: the implied acknowledgement of the inevitable perceptual and effective limits of any particular discursive entity. A formative, leaking axiom of undecidability at the heart of each such endeavour.
sites of execution: skin
shift.
As media theorist Friedrich Kittler highlights in his writings on the determining media environments of things like the introduction in the early 1980s and regular inclusion of a "protected mode" feature within the still predominant x86 family of instruction set architectures, logics of enclosure have a way of becoming immanent throughout media discourse networks, adding in layers of built-in blockades and restrictions that further remove users from the "real mode" of ostensibly full access to a computer’s original von Neumann architecture[1]. In an ongoing series of experimental works, Martin Howse (2013) has attempted to interrogate the nature of such computational enclosures, with their “separation of users and of their desires and affects,” and how “The possibility of transferring execution outside these sets of containers or black boxes into the world is resolutely denied.” In different ways, each of these pieces pose what Howse (cited in Sayej 2013) sees as a key question to be addressed:
where exactly do these seemingly abstract coded processes which seriously effects our lives, where do these take place? At first it seems simple, somewhere inside this machine or black box, a laptop, a smartphone, but looking at it closer there’s no easy answer. And I feel that this answer has to do with our skin and the Earth.
For Howse (with a nod to JG Ballard's Crash), one method or exploit for triggering a reacquainting of the faultlines of such a question is the act of shifting the site of an executable process from its typical or stabilised domain to a less typical or stable one. To this end, Howse carries out a range of experiments that, in one way or another, attempt to shift computational sites of execution into “new material (data), outside the particular confines of a trusted and identifiable process or skin," with Howse continually reforaging for and repurposing such arrangements towards alternative conceptions and sites of the executable. Looking at almost any of Howse's projects, a lingering question can be seen to take root: What is it that is executing here, or signalling to one?
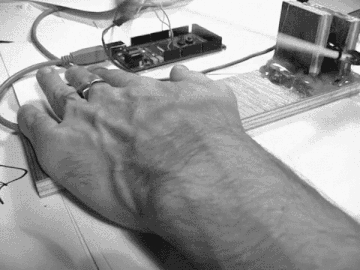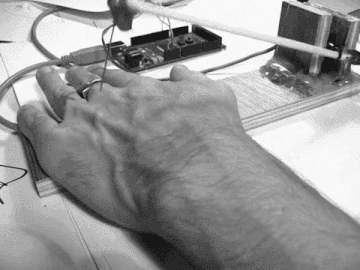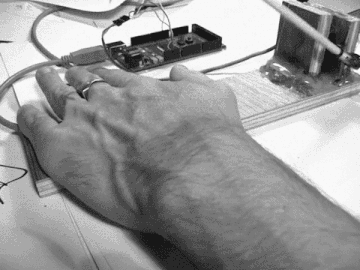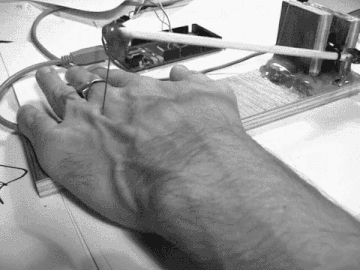
The following GIF is from a short film of an early prototype version of Howse’s pain registers project, which uses the ptrace()[2] system call to make readings of the operational codes, those “bare logical bones of computation” that are located on what Howse (2013) describes as the “questionable surface which divides software and hardware.” These readings of the opcodes that are running on a computer CPU are promiscuously transposed in real time, with Howse shifting the site of execution of code from the black boxed instruction pointer over to a machine-operated needle that carefully executes an up and down rhytmic pricking upon the skin of its user, writing patterned, piercing inscriptions on the skin’s surface according to the currently executing processes running on the user’s computer (such as the booting up or closing down of a Firefox web browser). This is in part a kind of reanimation of the semi-mythical "killer poke" from the earlier days of computing, in which “The computer crash originally referred to the disastrous impact of the hard disk’s read/write head on the shiny, information-rich surface of the hard drive platter […] eliciting violent hardware destruction” (Howse 2013). As Howse emphasises in this project, shifting sites of material execution are perhaps necessarily painful, potentially transgressively charged and informed by a ready courting of collapse, crashes, uncomputability.
In works like pain registers, there is an indication of how execution involves the setting of an enclosure so as to make the enclosed entities in question operable/computable/executable. Enclosures in this sense can be thought of as the establishing of a discretely defined site, but also in turn as a kind of skin, a surface, a grid, a volume, an object, a body, etc. Execution in computing ostensibly involves some kind of privileging of a symbolically enumerated layer and logic of enclosure in the name of executability, defining the rules and limits of its procedures, and in doing so, creating various kinds of executable sites, objects, bodies, spaces, etc. It mobilises a pact of structural impositions, both intensive and extensive. For Howse, enclosure also has a further dimension as a kind of protection (a “protected mode” - Kittler) from those things that know of no enclosure (plague, virus, earth, etc.).
Karen Barad (2007) gives the name of “agential cut” to any such acts of separation and distinction in the name of operability. In naming it so, Barad (2007, p.429) aims to highlight the ultimate impossibility of a clean cut and separation between something like an independent subject and an independent object, and instead situates the interpenetrative and ultimately relational nature of phenomena as the ontological ground from which “intra-actions” (rather than interactions, “which presumes the prior existence of independent entities/relata”) might then be discerned via any particular agential cut.
Barad invokes Donna Haraway’s (1992, p.300) emphasis on diffraction as a process of mapping “where the effect of differences appear,” with a specific focus on how any such figurations might act as diffractive entities whose powers of interruption and promise of reconfiguration can point to just such consequential differences and the situated nature of meaning. As Barad (2007, p.3) further elucidates (drawing from the example of quantum physics and its elucidation of the formative impact of the mediating apparatus and its observer effect), diffraction is particularly notable for its ability to highlight the way in which, “Matter and meaning are not separate elements. They are inextricably fused together […] Matter is simultaneously a matter of substance and significance.”
Given the way in which a large majority of computing today transpires for the everyday user at a level in which much of the interaction occurs in relatively restricted and virtualised interfaces, whereby the so-called “back-end” runnings and workings of the computational processes occur at often highly inaccessible or far removes, it is not surprising to see Howse and others working to explore this sense of material marks on bodies. Pain reigster's shifting of the site of execution from the processor register to the skin might be understood to be enacting a method of diffraction, materialising the cybernetic epistemology of a “unit” of information as “a difference which makes a difference” (Bateson 2000, p.315-318) via the self-same cybernetic apparatus and onto the user’s hand, so as to account for a sense of difference as “marks on bodies, that is, the differences materialized” (Barad 2007, p.89). Thus Howse (2013) speaks of the executable as “the real, that which is enacted and constructed by software in/as the world itself,” aiming to remove any sense of a privileged view from the outside and instead highlighting the interpenetrative entanglements and generative powers of matter and its execution across a range of intra-actively charged entities and practices.
Just as von Uexküll’s work in the laboratory set off a series of 20th century philosophical trajectories in relation to the example of the tick (e.g. Heidegger, Merleau-Ponty, Deleuze, Agamben), one sees in the likes of Howse, Kittler and Barad a diverse but nevertheless at times overlapping range of genealogical enquiries that constitutively bind technology and the mediating qualities of the apparatus to a certain physiological struggle that grounds the emergence of any formation of being in its various material supports (body, machine, earth, etc.). Media, despite their now even more seemingly malleable ability to configure and reconfigure nevertheless still form in relation to certain resistive sets of rules, protocols and perspectival logics that play out across an array of resistive materials, competing processes and bodies which they come into contact with. An ongoing interplay of affordances and potentials, whether of the body or at other scales, such as the expressive capacities and limits of the media inscription networks of the time or the indifferent environment and its nonetheless virulent, formative processes of entropy and material exchange. Each of these multi-scalar entities operating as situated and compositional bearers of a certain propensity for execution.
In its setting of limits and operative agential cuts, execution can in the process be seen to create certain sensible forms of skin or habitable enclosures, which in turn provide the possibility for dynamic encounters of power, transgression, mutation, etc. Howse (personal interview, 2015) speaks of execution's potential as a kind of magic. Magic as contagion, as an energetic current that becomes triggerable in the very executability of any particular process. The way in which putting a finite and completable rule/task/process like an algorithm into the world opens up an emergent current of executions in the processual interplay between the finite and its infinite possible encounters. One "magic" in this might be in how execution can be seen to enable the mobilisation of various drives towards fulfillment (Parisi & Fazi 2014) or the continuous seeking out of the physical and imagined limits of any such enclosed systems, and in so doing unleashes further potential frictions and resultant forms of desire around its ability or inability to fulfill its particular instruction set. These frictions point in turn to unfulfillable and unpredictable powers, drives, "materialist energies" (Fuller 2005), etc.
In each such instances: a discursive sedimenting of materials and energies, folding and coalescing into sites and ecologies of the executable. And within any such configurations: active agents and their executing practices as materially particulate sites and undulatory, resonating disturbance.
notes
[1] A stored-program computer for the processing, transmission and recording of inputs and outputs in which numerically encoded program instructions and data are stored in the same read-write, random-access memory and accessible via a common bus (though the application of protected mode style features is not limited to von Neumann architectures). For specific discussions of protected mode style features, see things such as the various NX bit ("No-eXecute") technologies used in CPUs to segregate areas of memory for use by either storage of processor instructions or for storage of data. Via such forms of segregation, such a memory protection feature can then mark certain areas of memory as non-executable. Thus in "real mode," a user should ostensibly be able to access and address all areas of the memory without any protection mechanism being employed. Like the tightly wound psychoanalytical schematics of Jacques Lacan, protected mode can be seen to act here "as both the enemy and co-existent partner of a Real Mode" (Kittler 2006, p.359-60). As Howse's work makes clear, the very notion of a protected mode might be questioned at several levels.
[2] Accompanying statement to a short video by Howse on the ptrace() call: "Date of origin: 1979. Author/inventor/context: Seventh Edition Unix, Bell Laboratories. An operating system call, first implemented in Version 7 of AT&T UNIX in 1979, which allows one piece of software (the parent) to observe, control, examine and alter any aspect of another process running on the same operating system. The ptrace call is commonly used to debug running code and can be considered as an active language, infiltrating and interrogating, snooping on and injecting code into living, running processes; an active language projecting a potential process promiscuity within the machine. Ptrace shifts the site of execution and is nowadays commonly viewed as an unnecessary security risk."
references
Barad, Karen. Meeting the Universe Halfway: Quantum Physics and the Entanglement of Matter and Meaning. London: Duke UP, 2007. Print.
Davis, Martin. The Universal Computer: The Road From Liebniz to Turing. London: CRC Press, 2012. Print.
Fuller, Matthew. Media Ecologies: Materialist Energies in Art and Technoculture. Cambridge, Massachusetts: The MIT Press, 2005. Print.
Guttag, John V. Introduction to Computation and Programming Using Python (Spring 2013 ed.). Cambridge, Massachusetts: The MIT Press. Print.
Haraway, Donna. “The Promises of Monsters: A Regenerative Politics for Inappropriate/d Others”. In Lawrence Grossberg, Cary Nelson, Paula A. Treichler (eds.), Cultural Studies. New York: Routledge, 1992, pp. 295-337. Print.
Howse, Martin. “Shifting the site of execution”. 1010 website. 2013. Web. http://www.1010.co.uk/org/shift.html
Ifrah, Georges. The Universal History of Computing: From the Abacus to the Quantum Computer. Tr. E. F. Harding. Wiley, 2001. Print.
Kittler, Friedrich. "Protected Mode." Tr. Stefanie Harris, in Martin Howse (ed.), [the] xxxxx [reader]. Berlin: xxxxx, 2006 [the article itself was originally published in 1991]. Print.
Parisi, Luciana & Fazi, M. Beatrice. "Do Algorithms Have Fun? On Completion, Indeterminacy and Autonomy in Computation." In Olga Goriunova (ed.), Fun and Software: Exploring Pleasure, Paradox and Pain in Computing. London: Bloomsbury, 2014. Print.
Sayej, Nadja. “Programming Computers with Dirt: Earthboot Powers PCs with Geological Energy.” Motherboard. October 22, 2013. Web. http://motherboard.vice.com/blog/programming-computers-with-dirt-earthboot-powers-pcs-with-geological-energy
Turing, Alan. "On Computable Numbers, with an Application to the Entscheidungsproblem." 1936. Print.
Uexküll, Jakob von. A Foray into the Worlds of Animals and Humans with A Theory of Meaning. Tr. Joseph D. O'Neil. Minneapolis: Unniversity of Minnesota Press, 2010 [originally published 1934]. Print.